As the importance of IT security becomes more and more apparent, system and organization control (SOC) examinations are being requested more often for third-party providers. If you know you need one, but you’re not sure what they are or why you need one, you’re not alone. There’s a dizzying array of categories and types of SOC reports — with various nuances and timelines for completion. We’ll help you determine what kind you need and what you need to know about it. Let’s dig into the fundamentals of SOC reporting.
What is a SOC report?
A SOC (often pronounced “sock”) report is an opinion provided by an independent certified public accounting firm as to whether an organization’s internal controls and processes are well structured and working properly. Essentially, it’s a third-party assessment of the risks associated with using an organization — for example, a software-as-a-service, third-party administrator, or payroll processor — with the goal of building trust between the organization and its customer. When performing a SOC examination and preparing a SOC report, the accounting firm looks at the organization’s internal control structure and whether it meets certain control objectives or criteria to manage various risks. While SOC reports aren’t a regulatory requirement, they’re a common contractual request of customers before they start doing business with you. It’s a formality that helps your customers manage risk associated with the activities they’re outsourcing to your organization.
Why get a SOC audit?
A common reason to get a SOC audit is because your customer requires one. But what if you could proactively provide your customers with a third-party report that supports the quality and effectiveness of your services and proves your organization as one that exhibits solid business practices? Engaging a firm to provide a SOC examination upfront is an excellent market entry strategy that can differentiate you from your competitors and demonstrate to sophisticated customers that you’ve got the right organizational controls in place. In addition to the marketing benefits, engaging a third-party for a SOC examination in advance can alleviate some of the pressures you might get from vendor questionnaires as you sign on new customers.
Categories of SOC examinations: What’s right for your organization?
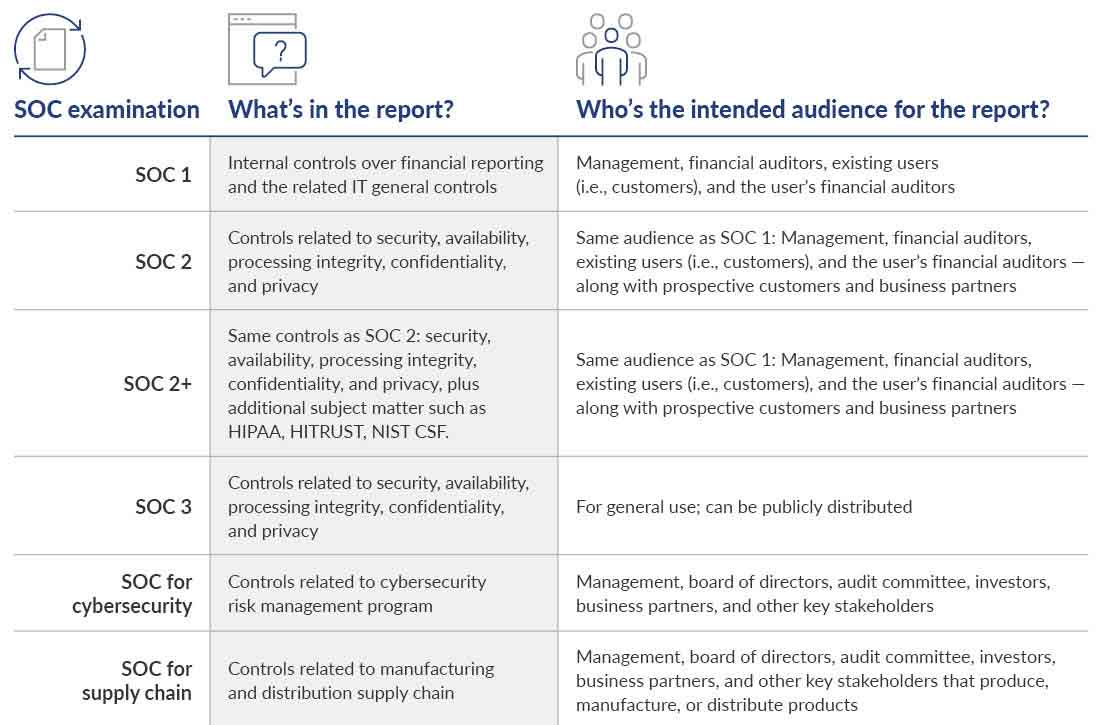
The three most common SOC examinations that can be performed are SOC 1, 2, and 3. There’s also “SOC for Cybersecurity” and “SOC for Supply Chain” that are used in specialized circumstances. The SOC examination that’s the best fit for you depends on the types of services you provide or the types of information you store, access, or process for your customers.
SOC 1 examination
SOC 1 includes content about controls at your organization that impact your customers’ internal controls over financial reporting. In short, if your company performs a service that potentially impacts your customers’ financials — for example, payroll processing — you should consider a SOC 1 examination and report. The intended audience for SOC 1 reports includes your organization, your auditors, your customers, and your customers’ auditors, and these reports shouldn’t be disseminated to anyone other than that.
SOC 2 examination
If you’re hosting or processing customer data where customers are concerned about that data's security, availability, or confidentiality, a SOC 2 report may be the best fit. SOC 2 addresses the effectiveness of controls related to one or all of the SOC 2 Trust Services Criteria: security, availability, confidentiality, processing integrity, and privacy. An extended SOC 2 report — called a SOC 2+ report — can include additional criteria from other frameworks such as HITRUST, HIPAA, or NIST CSF. SOC 2 report distribution is less restrictive than a SOC 1 report; you’re able to provide it to the same audience as SOC 1 reports, as well as prospective customers and business partners who understand the specifics of the report, but SOC 2 reports shouldn’t be publicly disseminated.
SOC 3 examination
A SOC 3 examination returns a general-use report that can be freely distributed. SOC 3 addresses similar matters as SOC 2, but due to its public nature, its report omits a description of the controls and the tests performed by the auditor. The intent of SOC 3 is to generate trust and confidence across a widespread audience without disclosing potentially sensitive information.
SOC for Cybersecurity
SOC for Cybersecurity provides assurance around your cybersecurity risk management program designed to provide background information for making informed decisions. These reports are often used by audit committees, boards of directors, or investors to ensure there are cyber risk management controls in place across an entire organization. With the latest SEC ruling on cybersecurity disclosures, if you want more assurance over your cybersecurity program to support your disclosures, a SOC for Cybersecurity report may be desirable.
SOC for Supply Chain
SOC for Supply Chain applies to your systems and controls if you’re part of a manufacturing and distribution supply chain. Specifically, it addresses controls related to your principal system objectives based on the applicable trust services related to security, availability, processing integrity, confidentiality, or privacy. It may also cover additional criteria such as sufficient availability of supplies.
What are SOC Type 1 or Type 2 examinations?
As an added twist, SOC 1 and SOC 2 examinations come in two types:
- Type 1: SOC Type 1 reviews the design of your controls and attests to the suitability of your procedures and internal controls at a single point in time.
- Type 2: SOC Type 2 addresses how your controls operate over a period of time — typically six months at a minimum, and often nine or even 12 months, depending on customer requirements.
The Type 1 report provides a lower level of assurance, but it can be completed relatively quickly and with less lead time. Type 2 reports provide more assurance to your customers but take longer to get a final report. Due to the time frame involved, it’s often a good idea to do a Type 2 proactively so you don’t miss out on potential customer requests.
Which SOC examination do I need?
To determine the right SOC examination and report for your organization, ask:
- Who’s the audience for the report?
- What’s driving the request for a report? Is it related to your customer’s internal control over financial reporting? Or is it more concerned with data governance, information security, and/or vendor management?
- What level of assurance is needed? Do your customers want assurance over both the design of organizational controls and how well they work?
Based on the answers to these questions, the following table will help you determine the SOC type you’ll need.
What should I look for in a firm that provides SOC examinations?
The job of a SOC service auditor is to make sure you’re meeting the examination requirements. However, an exceptional SOC service auditor will go beyond the basics to offer insights into what you can do better to strengthen your control structure and security compliance posture. When looking for a SOC service auditor, choose a reputable, well-known CPA firm that understands SOC guidelines and requirements. Pick a firm that wants to get to know you, takes the time to understand what your unique control structures and systems are, and is open to conversations about how they can help you. Finally, look for an organization with low staff turnover; it helps to have the same individuals work on your engagements each year so you won’t have to reexplain what you’re doing year after year.
The bottom line: The time to invest in SOC reporting is now
SOC reporting can be complex and may initially seem overwhelming. But the good news is SOC examinations and reports are a valuable investment that can improve your organization’s systems and controls maturity and open the door to a more robust customer base.





